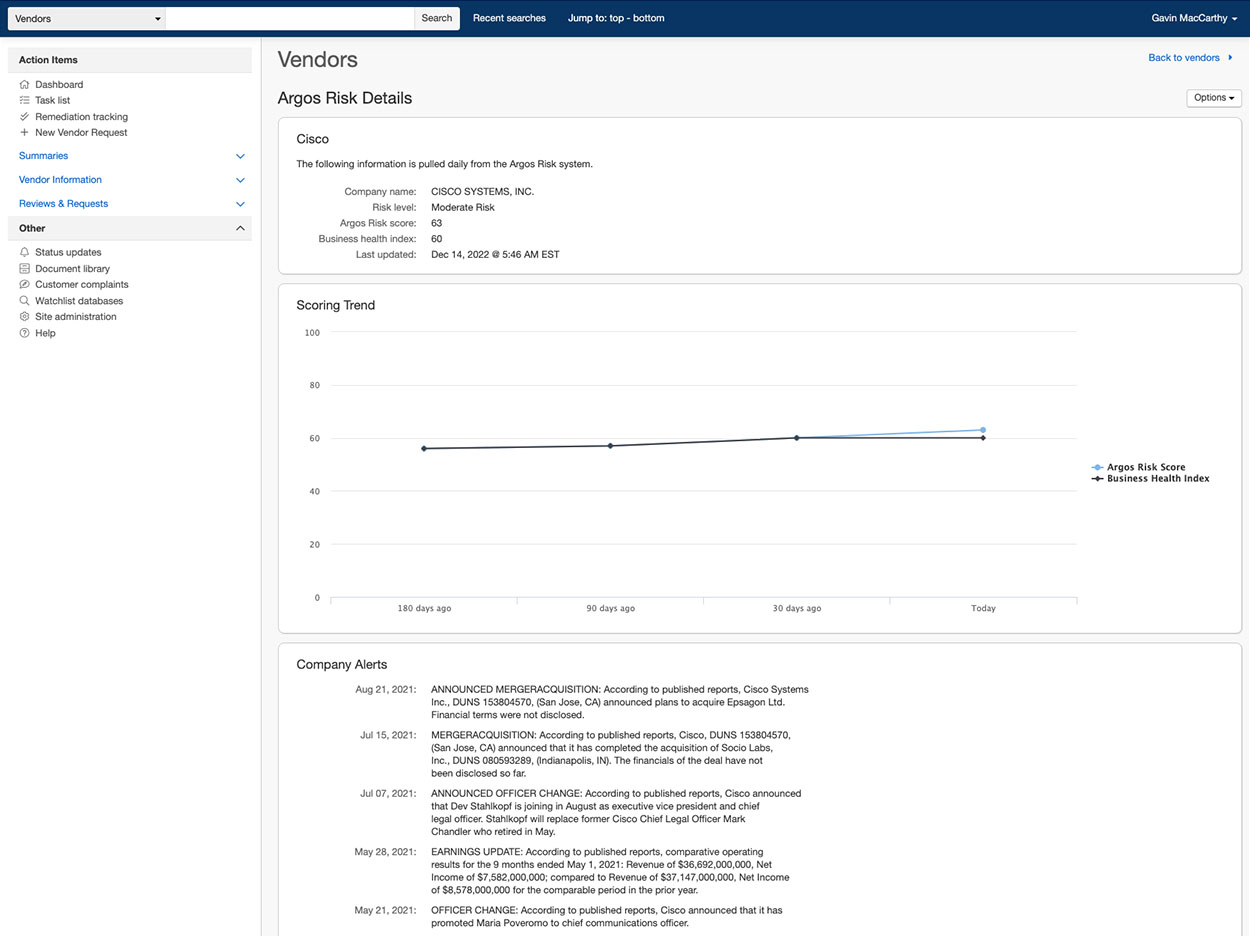
Strengthen Your Cyber Risk Strategy with Active Intelligence
AR Surveillance enhances Cyber and InfoSec vendor assessments by providing unbiased Cybersecurity rankings that automatically assess key network areas of commercial third-party web domains, powered by ArgosRisk
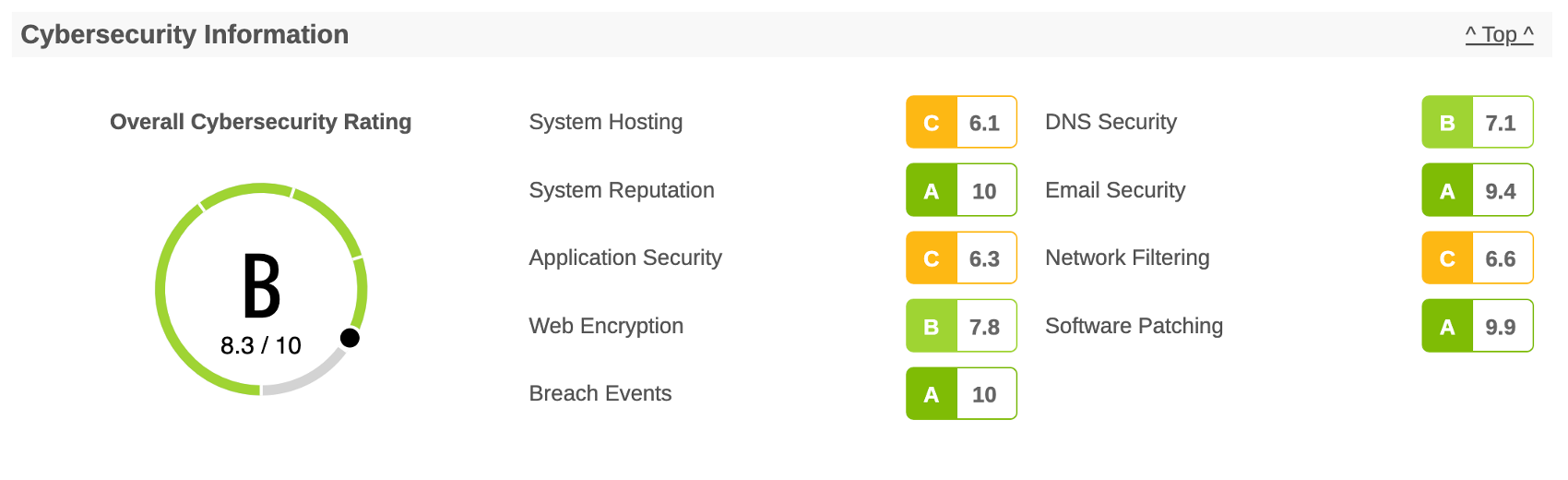
System Hosting
The System Hosting domain provides insight into the Internet vulnerabilities of the company, detailing the number of systems, the system hosting providers, and the system geolocations. How the organization has instantiated its internet presence is a driver of the complexity of managing IT security, privacy, and regulatory risk. In this domain, the system rates two criteria - the degree of system hosting fragmentation and the use of shared ip address hosting.
System Reputation
The System Reputation domain enumerates systems owned by the company that are communicating with monitored C2 servers, sinkholes, honeypots, or are exhibiting other hostile activity. The presence of the organization’s assets in threat intelligence feeds is an indicator of lack of consistent and effective security controls deployed to all systems necessary to prevent malware infection and system abuse.
Application Security
The Application Security domain assesses each discovered web application for compliance with widely accepted application security practices that can be assessed using passive techniques. Consistent deployment of web application security controls appropriate for the risk context of the system is important to defend against application level attacks. It is also an indicator that the company has a robust web application security program.
Web Encryption
The system used passive techniques to analyze web encryption security configurations. Correctly configured web encryption is essential to ensuring that communications are protected from eavesdropping and that people can verify the authenticity of the system. Addressing encryption issues also improves user experience, eliminating security alerts raised by the browser.
Breach Events
The Breach Event domain summarizes the breach events the organization has experienced. Recent breach events indicate gaps in the breach events protection program. Organizations with breach events occurring consistently over time very likely have ineffective breach prevention programs and material gaps in their information security program.
DNS Security
The DNS Security domain assesses the use of controls to prevent unauthorized modification of domain records resulting in domain hijacking. This domain also enumerates the DNS hosting providers to determine level of fragmentation. Control of DNS records is essential to keeping systems accessible.
Email Security
The Email Security domain analyzes the security configuration of email services. Email servers should be configured to encrypt email communications to protect email messages from unauthorized access. Domains should be configured to prove the authenticity of email messages to prevent spoofing.
Network Filtering
The Network Filtering domain analyzes the company networks and systems for the presence of unsafe network services and IoT devices. Proper control of the services exposed to the Internet is a basic security practice, as unsafe network services and IoT devices are a common vector for compromising systems and networks.
Software Patching
The Software Patching domain enumerates systems that are running end-of-life and vulnerable software. Because end-of-life software is not supported by the vendor, it cannot be patched against known security issues or new vulnerabilities that might be discovered, increasing likelihood of system compromise.